Deprecated - Google Workspace Setup
Warning: The options to set up single sign-on (SSO) through Google Workspace have changed. Organizations that use SSO will now see a New single sign-on tab on the Authentication settings page in Security and must set up new SSO connections by Oct. 31. This archived guidance for the now-obsolete configuration process will remain available to manage existing connections until the Oct. 31 deadline and will then be removed. For updated guidance to create or migrate SSO connections, see Google Workspace Setup.
 Archived single sign-on setup guidance for existing SSO connections only
Archived single sign-on setup guidance for existing SSO connections only
Your organization can use Google Workspace and its APIs to securely connect its users to technology. To enable your organization's Blackbaud IDs to sign in to Blackbaud solutions through Google, create a Google web application in your Google API Console and configure the following settings on the Authentication settings page in Security:
-
Your organization's primary Google domain or domain alias (To view your domains in the Google API Console, select Credentials, Domain verification.)
-
The client ID and secret generated when you create your application
To prevent inadvertent lockouts:
-
Complete configuration during a maintenance window for your organization's network.
-
Ensure that you have a Blackbaud ID outside of your claimed domains with access to the Authentication settings page.
Keep in mind that if you set up your Google Workspace connection and users with Blackbaud IDs on your claimed domains select Sign in with Google, they will encounter an error.
 1. Configure the Google application
1. Configure the Google application
Tip: To ease configuration, open the Authentication settings page in Security and your Google API Console in separate tabs of your browser.
-
In Security, select Authentication and then select Manage SSO settings.
-
Under Single sign-on, select Google Workspace.
-
Under Configure your connection, select Get started or Edit connection.
-
Enter the primary Google email domain to use with single sign-on (SSO) for your Blackbaud IDs.
-
In a separate browser tab, sign in to your Google API Console as the administrator for your Google Workspace connection.
-
Create a project or use an existing one on the domain.
-
For an existing project, select Select project, search for it, and select Open.
-
For a new project, select Create project, enter a name, browse to a folder location, and select Create.
-
-
To set up your consent screen, select Configure consent screen:
-
Select whether to register internal or external users, and then select Create. In most cases, you want to select Internal.
-
Configure the OAuth consent screen.
-
Under App information, enter an app name to display when users sign in to Blackbaud solutions through Google and a support email.
-
Under App domain, enter "blackbaud.com" as the authorized domain.
-
Select Save and continue.
-
-
Under Scopes, select Save and continue without specifying scopes.
-
Under Test users, select Save and continue.
-
Under Summary, review your selections and select Back to dashboard.
-
-
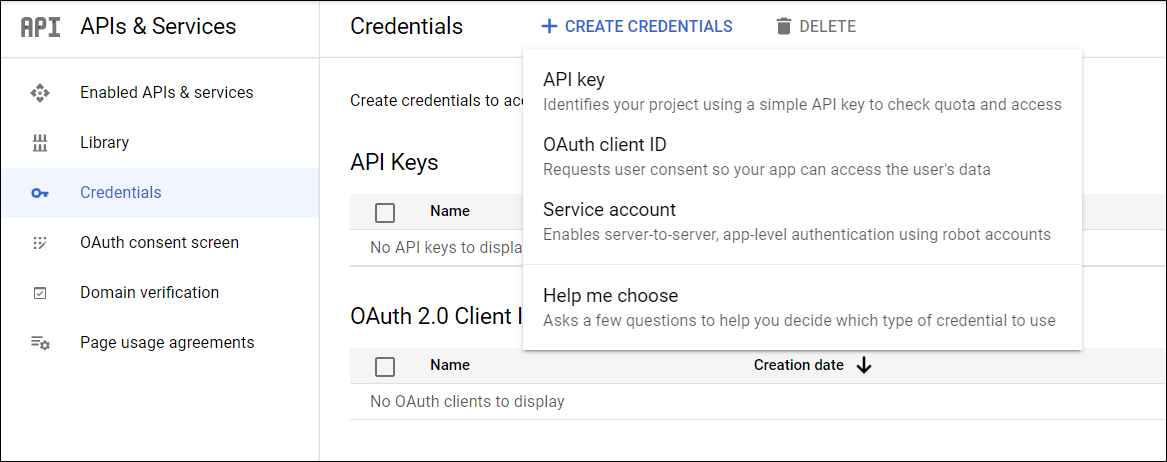
Select Credentials under APIs & Services, and then select Create credentials, OAuth client ID.
-
Create your application and its OAuth client ID.
-
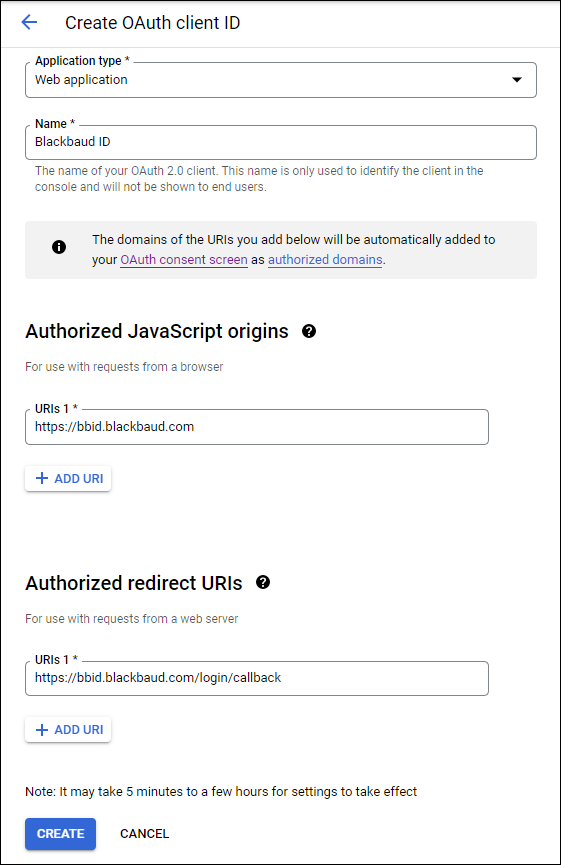
For the application type, select "Web application."
-
Enter a unique name to identify the application.
-
Under Authorized Javascript origins, enter "https://bbid.blackbaud.com" as Blackbaud's origin URI.
-
Under Authorized redirect URIs, enter "https://bbid.blackbaud.com/login/callback" as Blackbaud's callback URL.
-
Select Create.
-
Under OAuth client created, note the client ID and client secret for your project, and select OK.
-
-
Back on the Authentication settings page, enter the client ID and secret for your project.
Tip: To view the client ID and secret for your project in the Google API Console, select Credentials and select the project's name under OAuth 2.0 client IDs.
-
In your Google API Console, enable the Admin SDK API service.
-
From your project, select Library.
-
Search for and select Admin SDK API.
-
Select Enable.
-
-
Return to the Authentication settings page, and select Finish.
 2. Add email domains
2. Add email domains
To properly recognize and redirect users to your IdP when they sign in, identify which email domains your organization uses. For more information, see Claimed Email Domains.
 3. Test connection
3. Test connection
After you set up your Google application and claim your email domains, test the connection to verify your organization can now use its IdP to sign in to Blackbaud solutions. For more information, see Test Mode.
 4. Turn on Google Workspace
4. Turn on Google Workspace
After you set up your connection, you can turn on SSO through Google Workspace. When you turn on SSO, anyone who signs in to their Blackbaud ID with one of your claimed domains is redirected to your IdP. After they authenticate through your IdP, their Blackbaud ID:
-
Automatically redirects to your organization's login for future sign-ins
Tip: By default, users redirect to their Blackbaud ID profile when they sign in through your Google login. To instead open a different Blackbaud solution, edit the redirect. For more information, see Redirect Settings.
-
Uses your IdP for password updates, lockouts, and similar authentication management
To complete the connection to your IdP, select Learn about connecting SSO and Connect with Google Workspace.
Note: After you enable SSO, resend any pending invitations sent before the connection to Google Workspace.
Warning: After you set up your connection, if you change a user's email address, you create a new Blackbaud ID with the new address and will need to re-invite them — at that Blackbaud ID — to their Blackbaud solutions.
Tip: For a visual reference of the steps to set up Google as your identity provider (IdP) for an SSO connection with Blackbaud ID, see our Blackbaud Developers Conference presentation.
To clear your setup and start over, select Erase all single sign-on settings. For more information, see Deprecated - Single Sign-on Setup.
For information about how to set up a custom Security Assertion Markup Language (SAML) 2.0 app in your Google Workspace admin console for single sign-on (SSO), see Deprecated - SAML 2.0 Setup for Google Workspace.
If you have issues with your Google application, see SSO Connection Troubleshooting.