Deprecated - Okta Setup
Warning: The options to set up single sign-on (SSO) have changed. Organizations that use SSO will now see a New single sign-on tab on the Authentication settings page in Security and must set up new SSO connections by Oct. 31. This archived guidance for the now-obsolete configuration process will remain available to manage existing connections until the Oct. 31 deadline and will then be removed. For updated guidance to create or migrate SSO connections, see Single Sign-on Setup.
 Archived single sign-on setup guidance for existing SSO connections only
Archived single sign-on setup guidance for existing SSO connections only
Your organization may use Okta to securely connect its members to technology. To enable your organization's Blackbaud IDs to sign in to Blackbaud solutions through Okta, create an Okta application and configure its settings on the Authentication settings page in Security and your Okta account.
To prevent inadvertent lockouts:
-
Complete configuration during a maintenance window for your organization's network.
-
Ensure that you have a Blackbaud ID outside of your claimed domains with access to the Authentication settings page.
 1. Configure the Okta application
1. Configure the Okta application
-
In Security, select Authentication and then select Manage SSO settings under Single sign-on.
-
Under Single sign-on, select Use Okta.
-
Under Configure Okta connection, select Get started or Edit connection.
-
Enter your organization's name with only alphanumeric characters and dashes (no spaces), and select Next.
-
In a separate browser tab, sign in to your Okta account as an administrator, and create an application.
-
In your dashboard, select Admin, Applications, Add Application, and Create New App.
-
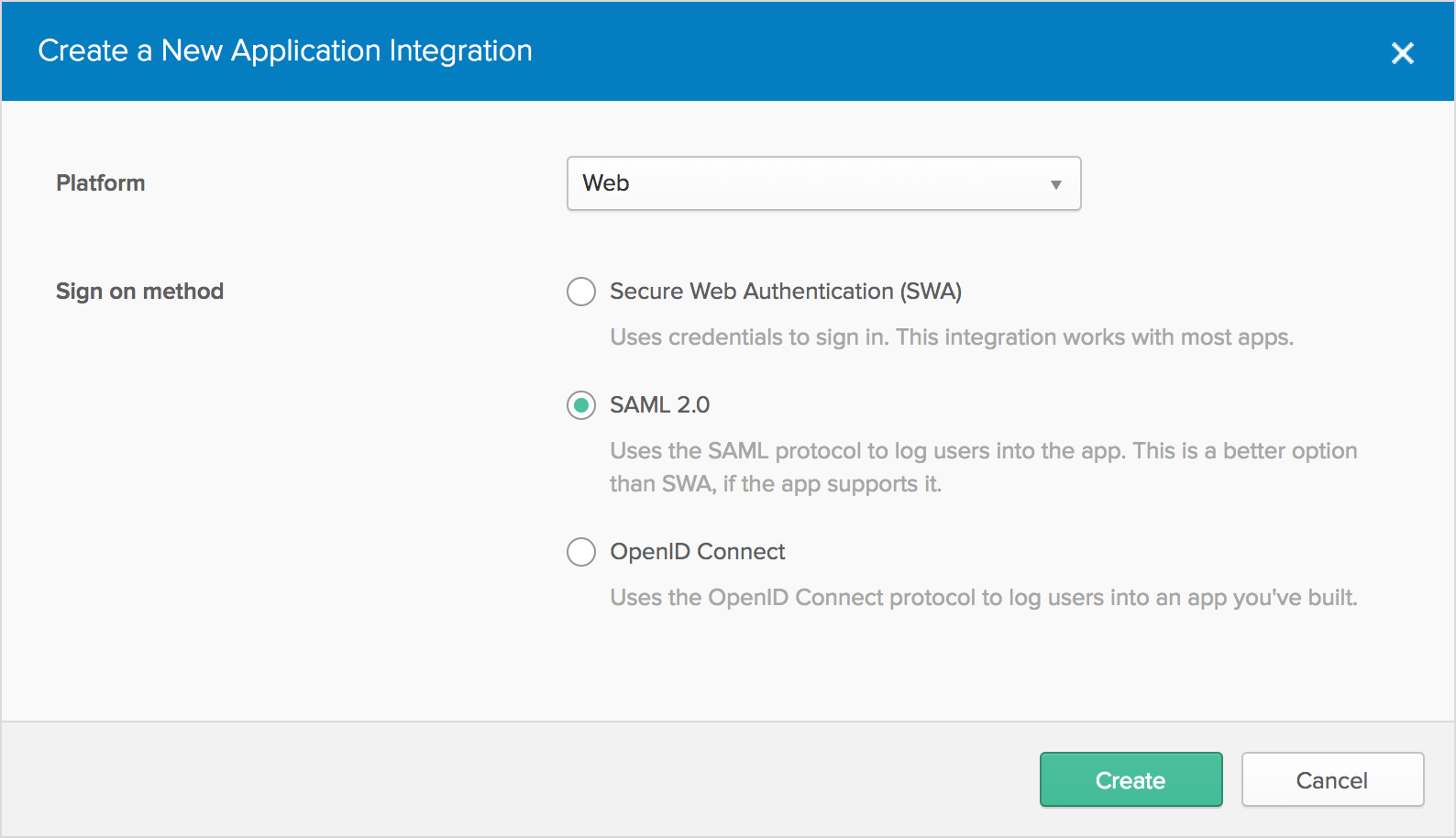
For Sign on method, select SAML 2.0 and Create.
-
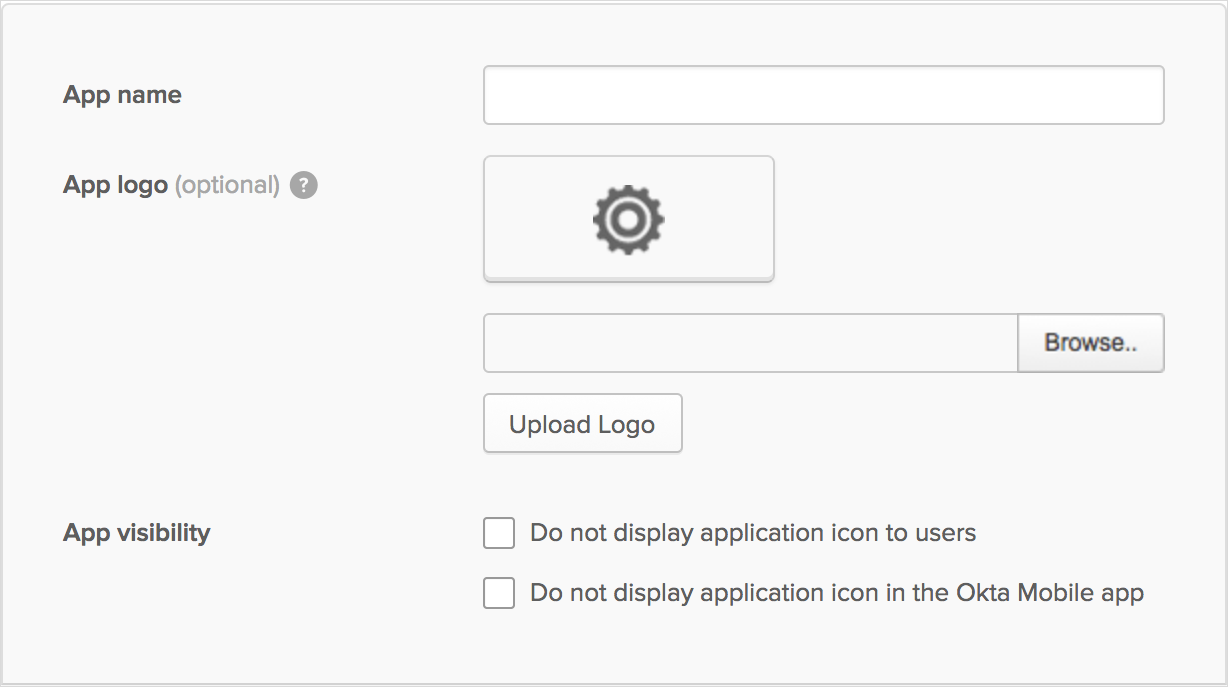
Under General Settings, enter a unique name to identify your application.
-
For App visibility, select both Do not display application icon to users and ...in the Okta Mobile app.
Tip: To enable members to easily access Blackbaud solutions, use redirect hints to create bookmark apps for the Okta dashboard or mobile app.
-
Select Next.
-
-
In your Okta dashboard, configure your application's SAML settings:
-
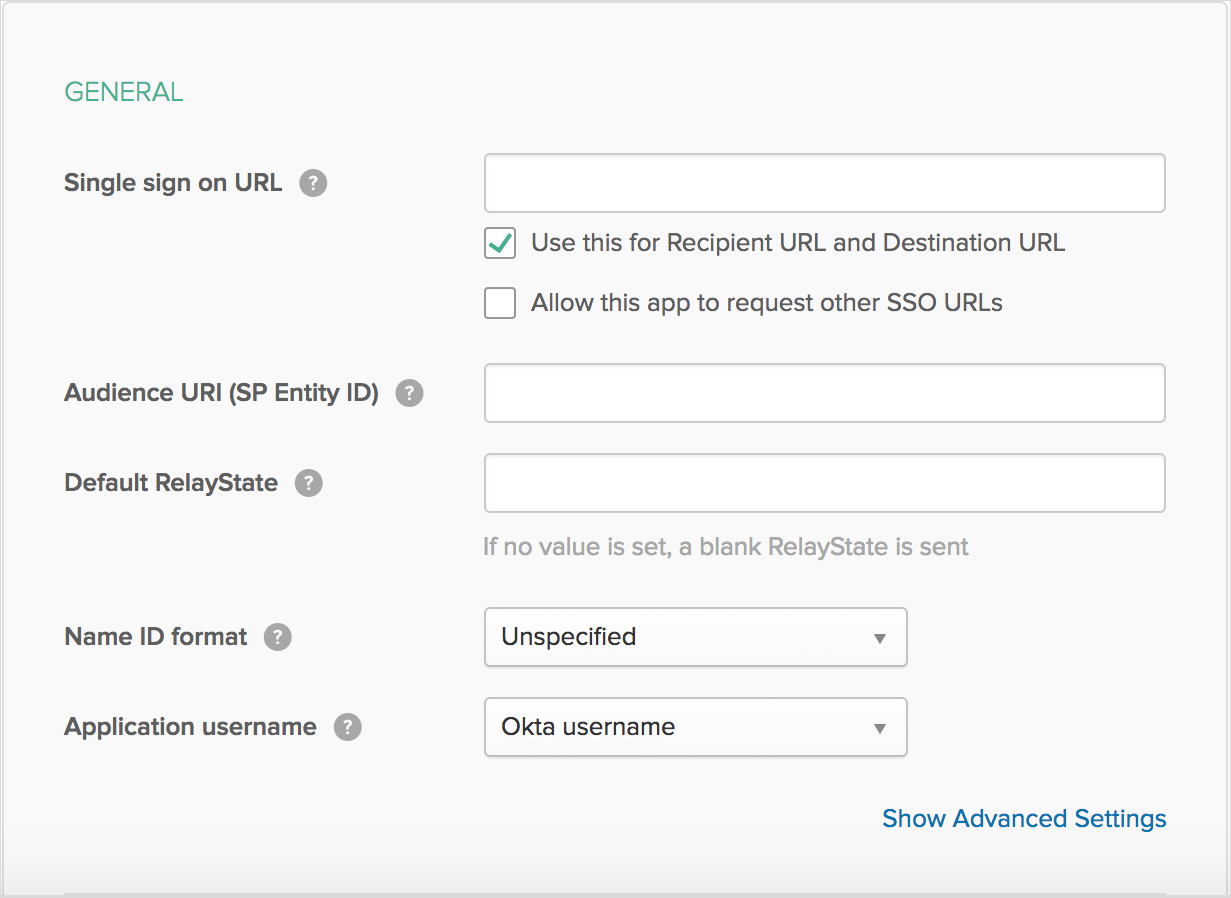
Under SAML Settings, paste or enter Blackbaud's callback URL — https://blackbaudinc.auth0.com/login/callback — in the Single sign on URL field.
-
In the Audience URI (SP Entity ID) field, paste or enter your organization's unique audience URI from Authentication.
-
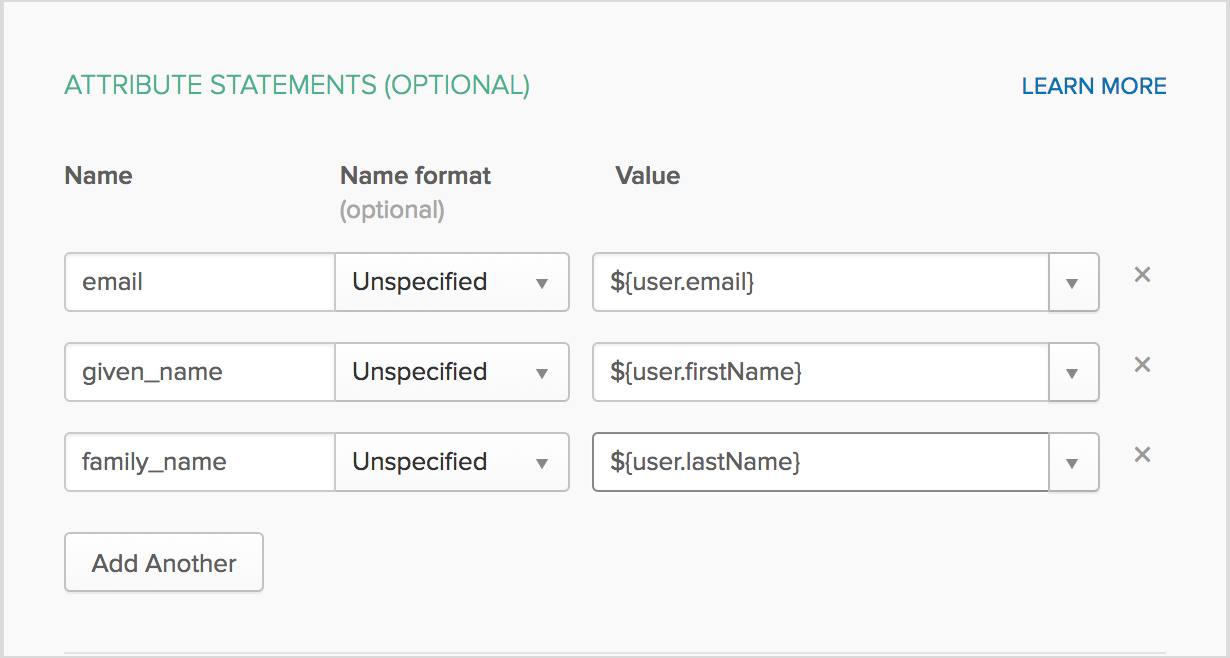
Under Attribute Statements, add the names and values used to identify email addresses and names. To add a new statement, select Add Another.
-
For email, enter ${user.email}.
-
For given_name, enter ${user.firstName}.
-
For family_name, enter ${user.lastName}.
-
-
Select Next.
-
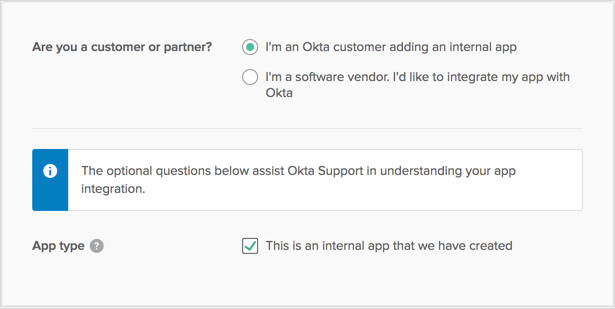
Under Feedback, select I'm an Okta customer adding an internal app and This is an internal app that we have created.
-
Select Finish.
-
-
On the Authentication settings page, select Next.
-
In your Okta dashboard, download your application's certificate.
-
In Applications, choose your new application and select Sign On.
-
Under Settings, select View Setup Instructions.
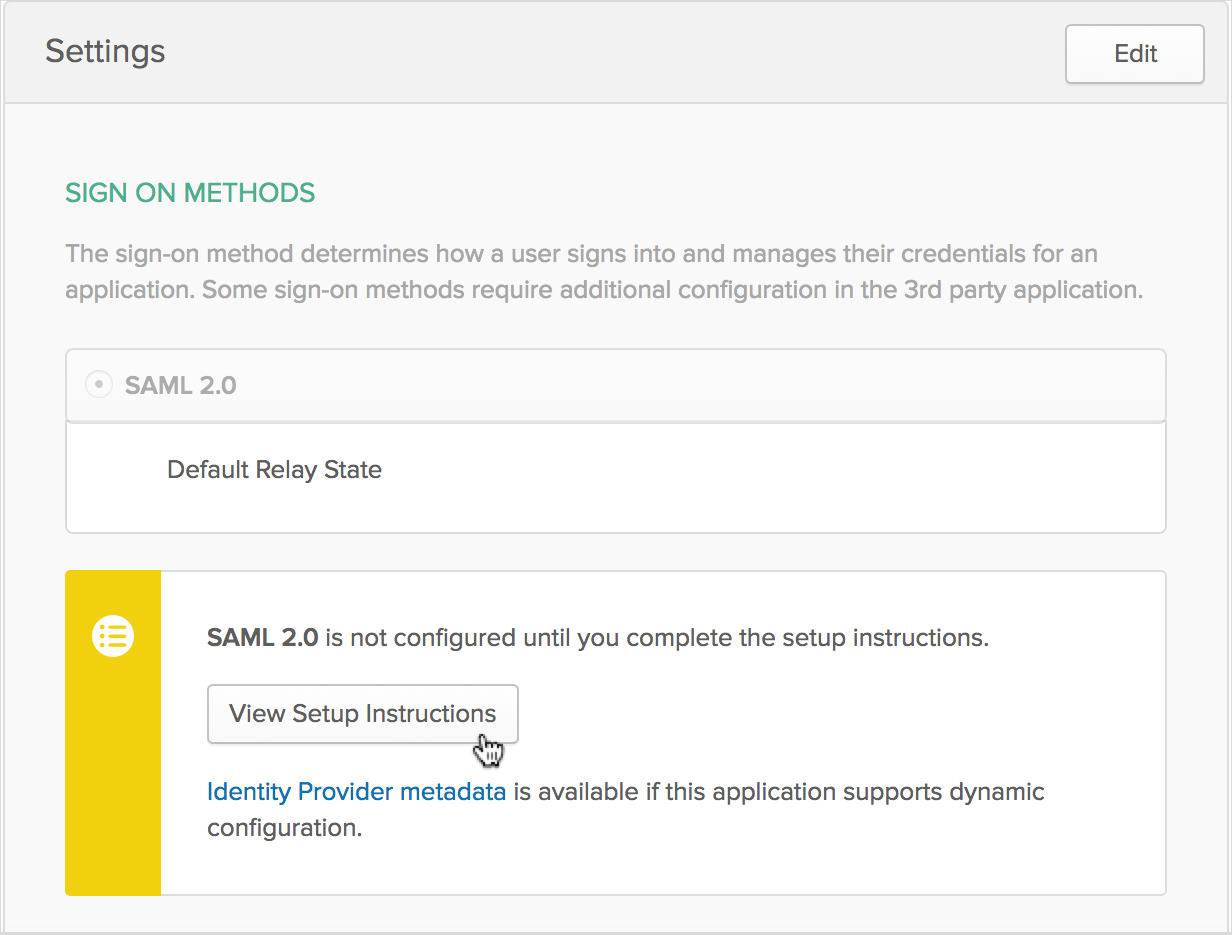
-
Under X.509 Certificate, select Download certificate.
-
-
On the Authentication settings page, enter details about your Okta application.
-
In the IdP SSO URL field, enter the application's SSO URL.
-
With a bookmark app, users can sign in to their Blackbaud solution directly from your Okta dashboard. In the IdP-initiated SSO URL field, enter the URL for your Blackbaud solution.
Tip: Your IdP-initiated SSO URL must use a Blackbaud ID-supported domain, such as blackbaud.com. For more information, see Redirect Settings.
For information about how to add a bookmark app in Okta, see Deprecated - Okta Bookmarks.
-
Under Signing certificate, select Choose file, and then browse to and select the certificate downloaded from your Okta account.
-
-
To enable members to sign in to Blackbaud solutions through your IdP, assign the application to them in your Okta dashboard.
-
In Applications, select Assign Applications.
-
Under Applications, choose the new application.
-
Under People, choose who should use the application.
-
Select Next.
-
Review the assigned people and select Confirm Assignments.
-
-
On the Authentication settings page, select Finish.
Tip: For more information about how to set up an Okta application, see Setting Up a SAML Application in Okta.
 2. Add email domains
2. Add email domains
To properly recognize and redirect members to your IdP when they sign in, identify which email domains your organization uses. For more information, see Claimed Email Domains.
 3. Test connection
3. Test connection
After you set up your Okta connection and claim your email domains, test the connection to verify your organization can now use its IdP to sign in to Blackbaud solutions. For more information, see Test Mode.
 4. Turn on Okta
4. Turn on Okta
After you set up your connection, you can turn on SSO through Okta. When you turn on SSO, anyone who signs in to their Blackbaud ID with one of your claimed domains is redirected to your IdP. After they authenticate through your IdP, their Blackbaud ID:
-
Automatically redirects to your organization's login for future sign-ins
Tip: By default, members redirect to their Blackbaud ID profile when they sign in through your Okta login. To instead open a different Blackbaud solution, edit the redirect. For more information, see Redirect Settings.
-
Uses your IdP for password updates, lockouts, and similar authentication management
To complete the connection to your IdP, select Learn about connecting SSO and Connect with Okta.
Note: After you enable SSO, resend any pending invitations sent before the connection to Okta.
To clear your setup and start over, select Erase all single sign-on settings. For more information, see Deprecated - Single Sign-on Setup.
If you have issues with your Okta application, see SSO Connection Troubleshooting.